Networking
Packet Telephony
What Is Packet Telephony? There has been a lot of confusion regarding packet telephony in two specific areas. First, packet telephony is not Internet telephones. Internet telephones are software packages sold predominantly through retail chains for hobbyists to place telephone calls over the Internet. They are generally awkward to use and offer poor voice quality. Packet telephony is also not the same as computer telephony integration (CTI). CTI is the loose integration of computer systems with telephony switches. Packet or IP telephony is the simultaneous and joined delivery of voice and data communications over a single, unified communications fabric based upon the Internet Protocol (IP). Packet telephony traffic will be delivered within the enterprise over an organization’s intranet and outside the enterprise initially over a circuit-switched fabric. Over time, as corporations develop extranets with their trading partners and as those partners install interoperable packet telephony systems, corporations will deliver packetized voice end-to-end outside of the enterprise.
Carrier Applications In the carriers, packet telephony is emerging as a key bypass technology. A new class of carriers, Internet telephony service providers (ITSPs), is building packet-based WAN networks to carry voice traffic. Even some traditional long-distance carriers are experimenting with packet-based WANs, primarily for service outside their regulated markets. New partnerships and consortia will emerge as these carriers attempt to create worldwide packet-based telephony networks.
Enterprise Applications In the enterprise, packet telephony will emerge in applications where the value proposition can be clearly articulated. This is likely to begin with specific applications in large organizations—applications utilizing the joined delivery of data and voice over a single infrastructure. Examples include next-generation call centers, new voice logging systems, and unified messaging: the joined receipt of voice mail and e-mail. Because of its radical technological departure, packet telephony will emerge at the fringe of organizations in value-added applications, not in the core premises telephony fabric. Given the critical importance of the telephony infrastructure, telecom managers will be reluctant to move the core of their business onto a completely new technology until the technology proves itself. Much of packet telephony’s present deployment is for toll bypass over WANs. Organizations are purchasing VOIP gateways to combine their phone and data infrastructures (or at least selected links in their infrastructures) primarily to high-tariff countries. Domestically, organizations with large branch office systems (such as banks) and a capillary data infrastructure to reach those branches are also exploiting the WAN data network to carry voice. In an odd reversal of the metaphor that sold T1 multiplexers for years ("voice pays for the circuit; data rides for free"), these customers have already installed and justified their data networks and are using spare capacity to carry intra-corporation voice traffic. Over time, as the business justification shifts to increased employee productivity and effectiveness, packet telephony will infiltrate the LAN fabric. Several events need to occur to effect this change. Much of the high cost of installing a LAN-based telephony system today lies in the infrastructure components (as opposed to telephone handsets or other client equipment). Within one year, these costs will reach a crossover point with traditional PBXs (Figure 6), and within two years they will be at a 30 percent discount to PBX costs. Another key issue is infrastructure reliability. Current LAN telephony systems use PC chassis for common infrastructure components. Many of these components lack redundancy, making the system vulnerable to component and system failure. However, a new generation of products built upon fully redundant, carrier-grade systems is coming to market. The 3Com Total Control ™ remote access concentrator is one such platform.
Packet Telephony Standards Four major organizations are working on various aspects of packet telephony standards: the International Telecommunications Union (ITU), the Internet Engineering Task Force (IETF), the European Telecommunications Standards Institute (ETSI), and the Institute of Electrical and Electronic Engineers (IEEE) under the auspices of its 802 committee. The ITU has developed the so-called "H.32x" family of standards related to video conferencing. Each H.32x standard pertains to a specific type of network, and refers to the appropriate subsidiary ITU standards for call processing, capability exchange, channel aggregation, media stream multiplexing, audio and video codecs, and data conferencing standards.
Packet Telephony Products The packet telephony products being delivered today are largely tactical, self-contained products that rely only tangentially on a larger infrastructure to deliver their value. The dearth of true systems products in this market space is attributable to the lack of an end-to-end, multimedia-ready IP packet infrastructure. Many customers are in the process of upgrading their entire fabric to support media-rich traffic, including voice and video. However, in the absence of a sizable installed based of media-enabled infrastructure, the packet telephony vendors are blocked from using the core of the data network and are left to deliver tactical products at the fringes. -- Saumitra [D9]
IP Addressing
Introduction
In the mid-1990s, the Internet is a dramatically different network than when it was first established in the early 1980s. Today, the Internet has entered the public consciousness as the world's largest public data network, doubling in size every nine months. This is reflected in the tremendous popularity of the World Wide Web (WWW), the opportunities that businesses see in reaching customers from virtual storefronts, and the emergence of new types and methods of doing business. It is clear that expanding business and social awareness will continue to increase public demand for access to resources on the Internet. There is a direct relationship between the value of the Internet and the number of sites connected to the Internet. As the Internet grows, the value of each site's connection to the Internet increases because it provides the organization with access to an ever expanding user/customer population.
Internet Scaling Problems Over the past few years, the Internet has experienced two major scaling issues as it has struggled to provide continuous and uninterrupted growth:
The eventual exhaustion of the IPv4 address space
The ability to route traffic between the ever increasing number of networks that comprise the Internet
The first problem is concerned with the eventual depletion of the IP address space. The current version of IP, IP version 4 (IPv4), defines a 32-bit address which means that there are only 2^32 (4,294,967,296) IPv4 addresses available. This might seem like a large number of addresses, but as new markets open and a significant portion of the world's population becomes candidates for IP addresses, the finite number of IP addresses will eventually be exhausted. The address shortage problem is aggravated by the fact that portions of the IP address space have not been efficiently allocated. Also, the traditional model of classful addressing does not allow the address space to be used to its maximum potential. The Address Lifetime Expectancy (ALE) Working Group of the IETF has expressed concerns that if the current address allocation policies are not modified, the Internet will experience a near to medium term exhaustion of its unallocated address pool. If the Internet's address supply problem is not solved, new users may be unable to connect to the global Internet!
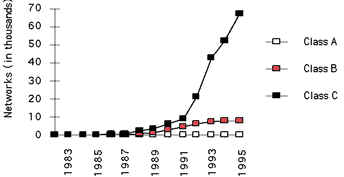
Figure 1: Assigned and Allocated Network Numbers
The second problem is caused by the rapid growth in the size of the Internet routing tables. Internet backbone routers are required to maintain complete routing information for the Internet. Over recent years, routing tables have experienced exponential growth as increasing numbers of organizations connect to the Internet - in December 1990 there were 2,190 routes, in December 1992 there were 8,500 routes, and in December 1995 there were 30,000+ routes.
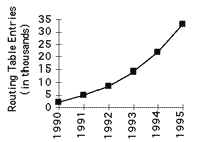
Figure 2: Growth of Internet Routing Tables
Unfortunately, the routing problem cannot be solved by simply installing more router memory and increasing the size of the routing tables. Other factors related to the capacity problem include the growing demand for CPU horsepower to compute routing table/topology changes, the increasingly dynamic nature of WWW connections and their effect on router forwarding caches, and the sheer volume of information that needs to be managed by people and machines. If the number of entries in the global routing table is allowed to increase without bounds, core routers will be forced to drop routes and portions of the Internet will become unreachable! The long term solution to these problems can be found in the widespread deployment of IP Next Generation (IPng or IPv6) towards the turn of the century. However, while the Internet community waits for IPng, IPv4 will need to be patched and modified so that the Internet can continue to provide the universal connectivity we have come to expect. This patching process may cause a tremendous amount of pain and may alter some of our fundamental concepts about the Internet.
-- Saumitra [D9]
Firewalls
Security has become one of the primary concerns when an organization connects its private network to the Internet. Regardless of the business, an increasing number of users on private networks are demanding access to Internet services such as the World Wide Web (WWW), Internet mail, Telnet, and File Transfer Protocol (FTP). In addition, corporations want to offer WWW home pages and FTP servers for public access on the Internet. Network administrators have increasing concerns about the security of their networks when they expose their organization's private data and networking infrastructure to Internet crackers. To provide the required level of protection, an organization needs a security policy to prevent unauthorized users from accessing resources on the private network and to protect against the unauthorized export of private information. Even if an organization is not connected to the Internet, it may still want to establish an internal security policy to manage user access to portions of the network and protect sensitive or secret information. An Internet firewall is a system or group of systems that enforces a security policy between an organization's network and the Internet. The firewall determines which inside services may be accessed from the outside, which outsiders are permitted access to the permitted inside services, and which outside services may be accessed by insiders. For a firewall to be effective, all traffic to and from the Internet must pass through the firewall, where it can be inspected . The firewall must permit only authorized traffic to pass, and the firewall itself must be immune to penetration. Unfortunately, a firewall system cannot offer any protection once an attacker has gotten through or around the firewall. It is important to note that an Internet firewall is not just a router, a bastion host, or a combination of devices that provides security for a network. The firewall is part of an overall security policy that creates a perimeter defense designed to protect the information resources of the organization. This security policy must include published security guidelines to inform users of their responsibilities; corporate policies defining network access, service access, local and remote user authentication, dial-in and dial-out, disk and data encryption, and virus protection measures; and employee training. All potential points of network attack must be protected with the same level of network security. Setting up an Internet firewall without a comprehensive security policy is like placing a steel door on a tent.
Benefits of an Internet Firewall : Internet firewalls manage access between the Internet and an organization's private network. Without a firewall, each host system on the private network is exposed to attacks from other hosts on the Internet. This means that the security of the private network would depend on the "hardness" of each host's security features and would be only as secure as the weakest system. Internet firewalls allow the network administrator to define a centralized "choke point" that keeps unauthorized users such as hackers, crackers, vandals, and spies out of the protected network; prohibits potentially vulnerable services from entering or leaving the protected network; and provides protection from various types of routing attacks. An Internet firewall simplifies security management, since network security is consolidated on the firewall systems rather than being distributed to every host in the entire private network. Firewalls offer a convenient point where Internet security can be monitored and alarms generated. It should be noted that for organizations that have connections to the Internet, the question is not whether but when attacks will occur. Network administrators must audit and log all significant traffic through the firewall. If the network administrator doesn't take the time to respond to each alarm and examine logs on a regular basis, there is no need for the firewall, since the network administrator will never know if the firewall has been successfully attacked! For the past few years, the Internet has been experiencing an address space crisis that has made registered IP addresses a less plentiful resource. This means that organizations wanting to connect to the Internet may not be able to obtain enough registered IP addresses to meet the demands of their user population. An Internet firewall is a logical place to deploy a Network Address Translator (NAT) that can help alleviate the address space shortage and eliminate the need to renumber when an organization changes Internet service providers (ISPs). An Internet firewall is the perfect point to audit or log Internet usage. This permits the network administrator to justify the expense of the Internet connection to management, pinpoint potential bandwidth bottlenecks, and provide a method for departmental charge-backs if this fits the organization's financial model. An Internet firewall can also offer a central point of contact for information delivery service to customers. The Internet firewall is the ideal location for deploying World Wide Web and FTP servers. The firewall can be configured to allow Internet access to these services, while prohibiting external access to other systems on the protected network. Finally, some might argue that the deployment of an Internet firewall creates a single point of failure. It should be emphasized that if the connection to the Internet fails, the organization's private network will still continue to operate--only Internet access is lost. If there are multiple points of access, each one becomes a potential point of attack that the network administrator must firewall and monitor regularly.
Limitations of an Internet Firewall An Internet firewall cannot protect against attacks that do not go through the firewall. For example, if unrestricted dial-out is permitted from inside the protected network, internal users can make a direct SLIP or PPP connection to the Internet. Savvy users who become irritated with the additional authentication required by firewall proxy servers may be tempted to circumvent the security system by purchasing a direct SLIP or PPP connection to an ISP. Since these types of connections bypass the security provided by the most carefully constructed firewall, they create a significant potential for back-door attacks Users must be made aware that these types of connections are not permitted as part of the organization's overall security architecture.
Internet firewalls cannot protect against the types of threats posed by traitors or unwitting users. Firewalls do not prohibit traitors or corporate spies from copying sensitive data onto floppy disks or PCMCIA cards and removing them from a building. Firewalls do not protect against attacks where a hacker, pretending to be a supervisor or a befuddled new employee, persuades a less sophisticated user into revealing a password or granting them "temporary" network access. Employees must be educated about the various types of attacks and about the need to guard and periodically change their passwords. Internet firewalls cannot protect against the transfer of virus-infected software or files. Since there are so many different viruses, operating systems, and ways of encoding and compressing binary files, an Internet firewall cannot be expected to accurately scan each and every file for potential viruses. Concerned organizations should deploy anti-viral software at each desktop to protect against their arrival from floppy disks or any other source. Finally, Internet firewalls cannot protect against data-driven attacks. A data-driven attack occurs when seemingly harmless data is mailed or copied to an internal host and is executed to launch an attack. For example, a data-driven attack could cause a host to modify security-related files, making it easier for an intruder to gain access to the system. As we will see, the deployment of proxy servers on a bastion host is an excellent means of prohibiting direct connections from the outside and reducing the threat of data-driven attacks.
Basic Firewall Design Decisions
When designing an Internet firewall, there are a number of decisions that must be addressed by the network administrator: The stance of the firewall; The overall security policy of the organization; The financial cost of the firewall; The components or building blocks of the firewall system. The stance of a firewall system describes the fundamental security philosophy of the organization. An Internet firewall may take one of two diametrically opposed stances: Everything not specifically permitted is denied; Everything not specifically denied is permitted. To be successful, organizations must know what they are protecting. The security policy must be based on a carefully conducted security analysis, risk assessment, and business needs analysis. If an organization does not have a detailed security policy, the most carefully crafted firewall can be circumvented to expose the entire private network to attack. How much security can the organization afford? A simple packet-filtering firewall can have a minimal cost since the organization needs a router to connect to the Internet, and packet filtering is included as part of the standard router feature set. A commercial firewall system provides increased security but may cost from U.S.$4,000 to $30,000, depending on its complexity and the number of systems protected. If an organization has the in-house expertise, a home-brewed firewall can be constructed from public domain software, but there are still costs in terms of the time to develop and deploy the firewall system. Finally, all firewalls require continuing support for administration, general maintenance, software updates, security patches, and incident handling.
Components of the Firewall System
After making decisions about firewall stance, security policy, and budget issues, the organization can determine the specific components of its firewall system. A typical firewall is composed of one or more of the following building blocks:
Packet-filtering router
Application-level gateway (or proxy server)
Circuit-level gateway
Firewalls should form an integral part of any network which if not implemented could lead to embarrassments like the break in at BARC.
—Saumitra [D9]
